How the next generation will make Iowa a leader in cybersecurity
Words, Photos, Graphic and Video by Tim Webber
Hilton Coliseum, on the campus of Iowa State University in Ames, Iowa, has hosted its fair share of basketball games. But over the weekend of April 21, with the college basketball season long past, the hallowed stadium opened its doors for a competition that involved a different type of net: the internet.
Nearly 500 high school students from across Iowa traveled to Ames to participate in the IT Olympics, sponsored by the HyperStream branch of the Technology Association of Iowa. On the Coliseum’s hardwood floor, students participated in events ranging from cyber defense to robotics to app development while coaches and volunteers roamed about. Still more events spilled out into the concourse areas.
In its ninth year, HyperStream helps fulfill the goals of Iowa governor Terry Branstad’s STEM initiative by improving technology education and literacy in the state of Iowa. The taste of competition at the IT Olympics leads some students to consider careers in related fields they hadn’t previously considered.
“I did one competition and I was hooked,” said Daniel Limanowski, a sophomore at Iowa State who now directs the cyber defense event at the IT Olympics. “They’re just a ton of fun. To be able to form a team and just protect against hackers and work with other teammates — that’s just a lot of fun.”
The IT Olympics appeal to hardcore technology junkies as well as those with a casual interest in the field.
“Because of the different tracks, there’s something for everyone,” said Emily Pottebaun, a junior at Adel Desoto Minburn High School who participated in the cyber defense event. “People will invite their friends, and people will come in if they’re interested and kind of get roped along and end up enjoying it.”
That’s important, because the state is banking on those types of success stories to ensure the future of cybersecurity in Iowa and the Midwest.
The Cyber Alliance
“There’s a misconception that you have to fly 2,000 miles or however far it is in either direction next to a large body of water. You can find a job next to Gray’s Lake, a small body of water.” Dr. Doug Jacobson, Professor of Computer Engineering at Iowa State University
On December 21, 2015, Branstad signed an executive order declaring cybersecurity a top priority for his administration. Following the order, the state crafted a detailed strategy for both dealing with large-scale cyber attacks and building up cyber infrastructure within the state.
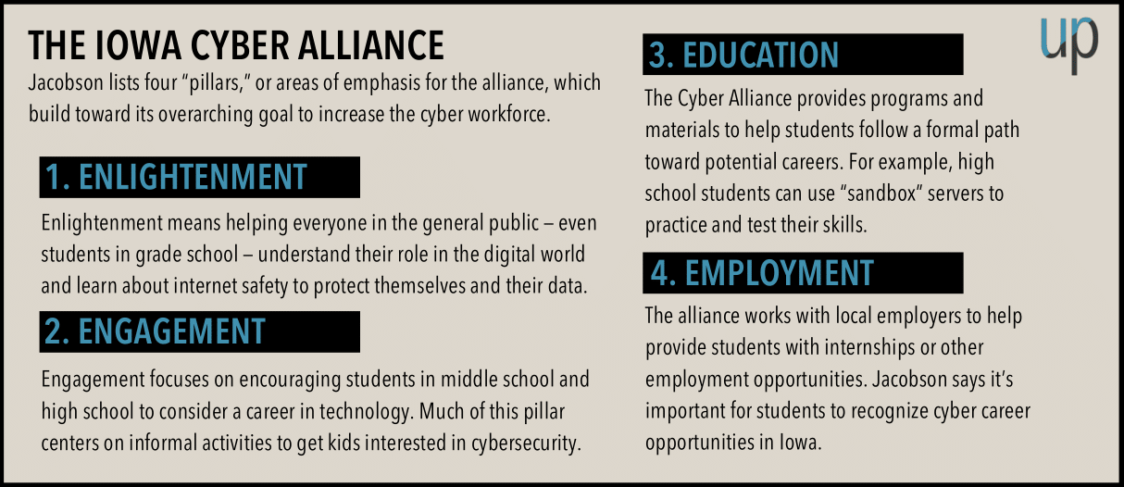
An offshoot of the state’s strategic plan is the Iowa Cyber Alliance. The alliance aims to increase the size of the cyber workforce in the region and help educate technological laypeople about ways to protect their assets.
Dr. Doug Jacobson, a professor of computer engineering at Iowa State and a leader of the alliance, said the initiative is working with local employers to help students gain experience in the field and show them that cybersecurity is not confined to the coasts.
“There’s job potential,” Jacobson said. “There’s a way to stay in Iowa, if they want to, to work in cyber.
“There’s a misconception that you have to fly 2,000 miles or however far it is in either direction next to a large body of water. You can find a job next to Gray’s Lake, a small body of water.”
 The erroneous perception that there are no cybersecurity jobs in the Midwest goes hand in hand with another:
The erroneous perception that there are no cybersecurity jobs in the Midwest goes hand in hand with another:
“One of the other misconceptions is Iowa is not targeted. Why would anybody pick on mom and dad’s manufacturing shop in Ottumwa, Iowa?” Jacobson said. “There’s plans there. There’s stuff there. There are things of interest.”
Midwesterners are targeted by cyber criminals like everyone else, in part because the criminals often don’t know where their target is even located. Often, the hackers send out a wide net in hopes of catching at least a few victims.
“It costs them no money,” Jacobson said. “They can carry out a massive attack with no resources, no capital investment, and all it takes is a small number of hits. When your investment’s almost zero, return on investment’s almost infinite. It’s a pretty lucrative business to be in.”
Jacobson noted common scams involving phony emails pretending to be from US Bank or Wells Fargo or dangerous attachments or links. These sorts of techniques can apply to a wide variety of people, so they’re likely to find more victims.
“Technology’s taken it to a point where (security) is pretty good,” Jacobson said. “But the hackers still want in. And the weak point is the person.”
The Cost of a Breach
For businesses, the cost of suffering a cyber attack is considerable. In an annual study, IBM found the average damage cost of each data breach to be $4 million. The total global cost of cybercrime could reach $2 trillion by 2019 and shows no signs of slowing. The International Data Group measured the annual financial hit from the loss of trade secrets alone to be worth 1-3 percent of a country’s gross domestic product.
But it’s not only large businesses that are affected by cybercrime. A study by the Ponemon Institute found that half of small and mid-sized businesses had been attacked within the past year. The damage from these breaches averaged nearly $1 million, a cost that can be crippling to small businesses.
Cybercrime is one of the fastest and most lucrative ways for criminals to make money. And it’s still difficult to track down the hackers.
“The whole television genre of being able to track back who’s doing it in real time and figure out who — no. No,” Jacobson said. “Half the time we don’t know who’s doing it. We can’t prove who’s doing it. A lot of times it’s not that important anyway.”
A significant number of data breaches occur not as a direct result of a malicious actor hacking into the system, but instead as a result of humans being careless. That same Ponemon Institute study found that more than half of small business employees use the same password for everything within the company. Perhaps unsurprisingly, most of those businesses’ data breaches occurred because of compromised passwords.
Even in the event of a cyber attack, small businesses feel ill-prepared. Just a third of those surveyed in the Ponemon report said they could adequately detect and block most cyber attacks. It’s no wonder a study by Cisco estimated that there are 1 million unfilled cybersecurity positions worldwide.
The jobs are there, even in Iowa. Businesses just need well-trained employees to fill them.
Iowa’s Plan
“From a cyber disaster standpoint, we’re probably better prepared than a lot of states,” Jacobson said. “I know we’re better prepared than a lot of states.”
For his part, Jacobson believes Iowa is in a good spot. The state has been preparing for years to deal with a large-scale cyber disaster, should one ever happen, by constructing the appropriate bridges of communication between departments.
“One of the things that’s been shown in the past in massive cyber events is that organizations haven’t built those human bridges,” Jacobson said. “So in the event of a cyber (attack), you run around not knowing who to talk to. Who’s the local FBI agent? Do you have a relationship with them?”
The cybersecurity strategy released last year helps outline a response plan in the case of a cyber attack. The state information office has been working with the Iowa national guard to coordinate their response, should an attack occur.
“From a cyber disaster standpoint, we’re probably better prepared than a lot of states,” Jacobson said. “I know we’re better prepared than a lot of states.”
In the meantime, Iowa is working through the Cyber Alliance to build up its human capital of cybersecurity skills. Part of that involves educating the next generation and piquing their interest in technology, and another part involves helping the rest of the public become cyber literate. The alliance has materials to facilitate education for students as young as third grade.
“I think we’re doing a fair job of trying to get the general public engaged, but that’s a tough piece,” Jacobson said. “You don’t want to run around and scare them, which is easy to do. Anyone in cybersecurity can go give a talk with a bunch of senior citizen-type people, and you can scare them to a point where they won’t touch a computer again. That’s not very beneficial.”
The alliance also offers programs to help those already in the workforce obtain IT skills — a career move that can lead to hefty salary increases.
But there’s one thing missing from the governor’s plan: money.
“The governor’s strategic plan has a lot of pieces in it,” Jacobson said. “The one piece it does not have in it is there’s not a single dollar assigned to any of the pieces.”
How To Protect Your Data
Individuals, on the other hand, can easily take the necessary steps to protect themselves from cyber attacks at a minimal cost.
The conventional advice, while rote, is important to follow. The first step? Simply be careful. Be wary of links and attachments that are sent from strangers, but also scrutinize those that were sent unsolicited from friends.
“I think this is what’s hard sometimes — and again, not to be stereotypical — people in the Midwest tend to be very trusting of everybody,” Jacobson said. “So it’s hard to sit there and tell somebody not to trust something. Because it’s in their nature to. That’s why we all pull over to the side of the road and help somebody. We love helping people. So, especially when it’s a stranger, you need to look at it with the eyes of not trusting them. And that’s hard to convince people to do.”
Jacobson also recommends backing everything up frequently, to either the cloud or physical hardware. In addition to having the security of a fallback in case of technological issues, backing up data can help combat the recent proliferation of ransomware attacks.
Ransomware typically enters a system covertly, through a downloadable file or unsecured network. From there, it virtually takes data “hostage,” by either preventing its owner from accessing it or threatening to release it publicly unless the owner pays a ransom to recover it.
An IBM study found a 6,000 percent increase in ransomware incidents last year, with perpetrators raking in around $1 billion altogether. Forty percent of all spam emails sent last year contained ransomware.
Still, the easiest way to avoid becoming the victim of a cyber attack is to simply stay vigilant and be prepared for the worst-case scenario.
The Future

Volunteers at the IT Olympics work to resolve a network issue during the Cyber Defense competition on April 21 in Ames, Iowa.
The students seated at the tables on the hardwood floor of the Hilton Coliseum are preparing for the worst-case scenario.
They have taken the last three to four weeks to set up and secure a collection of servers. They have a wide array of options available to them as they work to optimize their setup — they essentially have free rein over their servers. On this, the first day of the IT Olympics, they work to complete their security systems with the help of volunteers like Limanowski. Each team works in a cramped area isolated from the other teams by black curtains.
On the second day, a team of cybersecurity professionals and graduate students will put their servers to the test over a grueling eight-hour period. Just as in the real world, the students are trying to protect important data from the hackers.
“We try to develop the scenarios to be as realistic as possible within the realms of a four-week competition and two-day on-site phase,” Limanowski said. “The virtualization software and the server cluster and everything that we run really mimics the internet. It gives quite a realistic experience for the teams.”
Although the students are tackling professional-level challenges, many of the students find success beyond their grade level.
“We have quite a wide range of competitors, so you have students that absolutely blow you away with their knowledge,” Limanowski said. “The things that they’re setting up, they’re well above where a lot of people are, and especially where I was at that age.”
But an encyclopedic knowledge of cybersecurity isn’t a requirement to compete.
“You also have a lot of people who are just kind of there to see what it’s like, to experience what working in an IT field would be like, what cyber defense really means, and just learning and starting out from that point,” Limanowski said. “Maybe they don’t know that much about programming and they just want to get involved.”
Pottebaun falls closer to the latter category. She said the IT Olympics were her first experience with cyber defense competitions. She’s still more than a year away from graduating high school, but she said the event has led her to consider pursuing computer science in college and as a career.
“Honestly, I decided just to try it just to try something new, and I just really enjoyed it,” Pottebaun said. “I enjoyed the creativity it allowed for.”
Pottebaun’s interest — and the similar interest shared by most of the other 500 students at the IT Olympics — is a good sign for the future of cybersecurity in the Midwest.